Last year VMware announced FedRAMP High Authorization for vRealize Suite Cloud for the U.S. Public Sector and I was lucky to be part of the Project for VMware Aria Operations for Logs SaaS (vRLI Cloud)
In this blog, we will explore FedRAMP in more detail,
- What is FedRAMP
- Benefits
- Requirements
- Authorization Process
- Compliance Process
- Documentation
- Security Impact Categorization
- Identify Security Controls & Implement Security Controls
- Create SSP
- Assess
- Authorize
- Continuous Monitoring
- Documentation
What is FedRAMP Authorization
FedRAMP, or the Federal Risk and Authorization Management Program, is a US Federal government-wide program that provides a standardized approach to cloud security assessments and authorizations.
The primary goal of FedRAMP is to provide a consistent and repeatable approach to assessing the security of cloud-based systems. The program aims to ensure that federal agencies can safely adopt cloud services without having to perform their own in-depth security assessments.
Benefits
Following are the benefits of using FedRAMP
- Improved Security: It provides a standardized approach to cloud security assessments, which helps to improve the overall security posture of federal agencies.
- Streamlined Compliance Process: It simplifies the compliance process for federal agencies, as they do not have to perform their security assessments.
- Reduced Risk: It also helps to reduce the risk of data breaches and cyber attacks by implementing a comprehensive set of security controls and procedures.
- Increased Confidence: FedRAMP provides federal agencies with increased confidence in the security of their cloud-based systems, as they are subject to regular security assessments and authorizations.
- Cost Savings: As the organizations don’t have to perform their own assessments it can save time & money
Requirements
To be compliant with FedRAMP, Cloud Service Providers (CSP) must meet the following set of security requirements
- Federal Information Processing Standards (FIPS) Compliance: CSP must comply with FIPS 199 & 200, which provides guidelines for computer and information security. This will help identify the impact level.
- Security and Privacy Controls: CSP must implement a range of security and privacy controls, including encryption, access control, and incident response as described in the National Institutes of Standards & Technology (NIST) 800-53, security control baseline for moderate or high impact levels.
- System Security Plan (SSP): CSP must develop an SSP that outlines their security controls and procedures.
- Security Assessment: CSP must undergo a comprehensive security assessment to identify and mitigate potential risks.
- Third-Party Assessment: CSP must undergo a third-party assessment of their security controls.
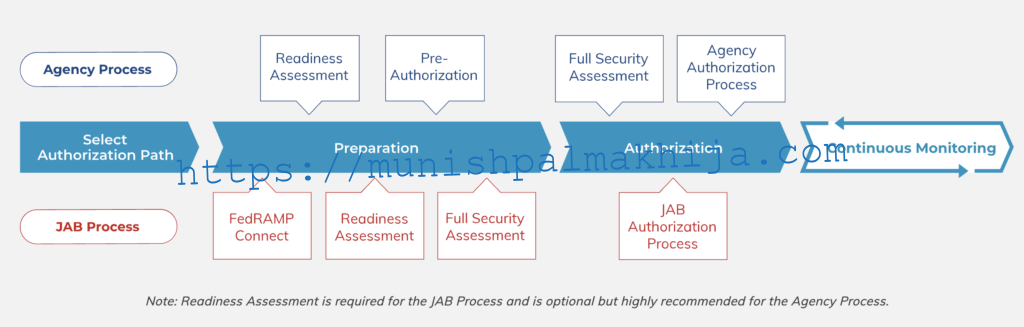
Authorization Process
There are two ways to authorize a Cloud Service Offering (CSO) through FedRAMP, through an individual agency, or the Joint Authorization Board (JAB)
Compliance Process
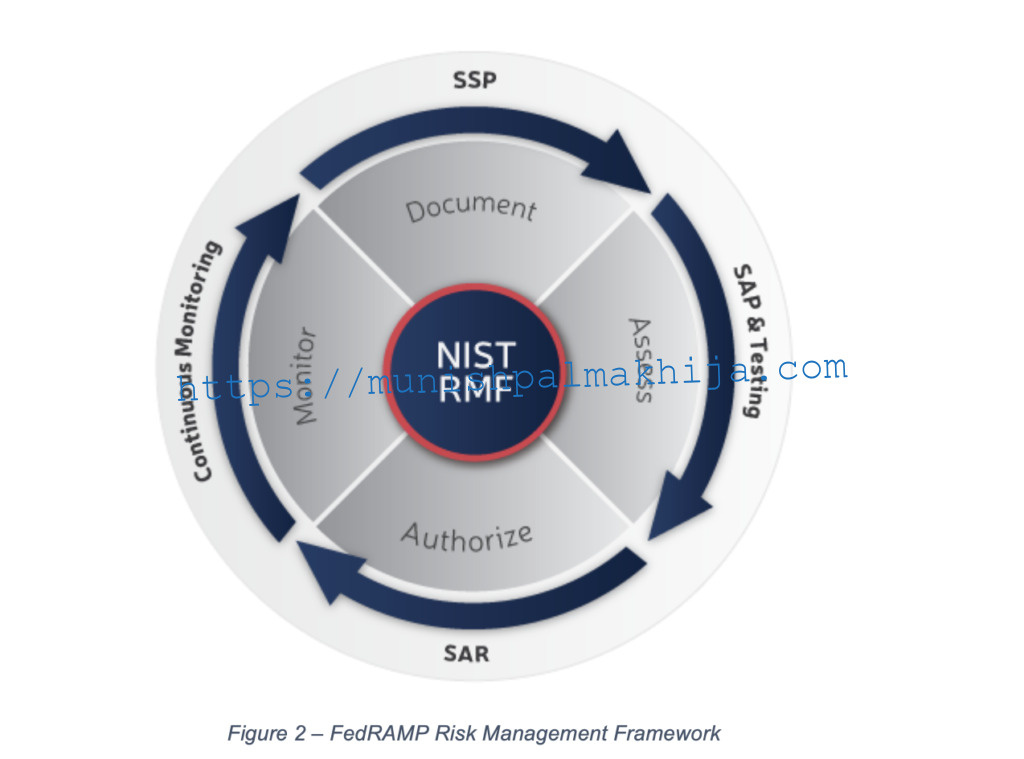
The following high-level steps from the FedRAMP Risk Management Framework outline the process to achieve FedRAMP compliance.
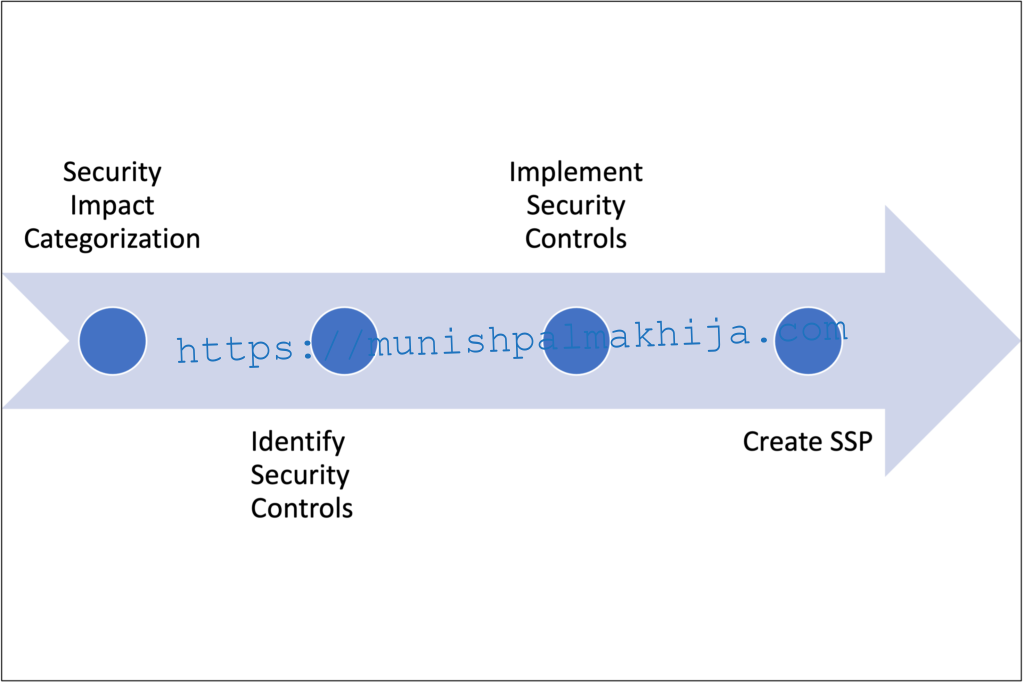
Documentation
Identifying the security controls and documenting the implementation plan in the SSP is a critical step in the process of FedRAMP Authorization
The following figure provides a high-level view of the process
The below section provides a brief description of each step included in the process
Security Impact Categorization
- Impact Level 2 (Low):
- Information processed at this level is designated as low-impact.
- Systems at this level typically handle unclassified information that is not deemed sensitive.
- Security controls focus on basic safeguards to protect against unauthorized access and disclosure.
- Impact Level 4 (Moderate):
- Information processed at this level is categorized as moderate-impact.
- Systems at this level handle sensitive but unclassified, information.
- Security controls are more stringent compared to Level 2, covering a broader range of safeguards.
- Impact Level 5 (High):
- Information processed at this level is considered high-impact.
- Systems at this level handle classified information up to the “Secret” level.
- Security controls are comprehensive and stringent to protect against unauthorized access, disclosure, and tampering.
- Impact Level 6 (High):
- Introduced as part of the FedRAMP High Baseline, Level 6 is an extension of Level 5 for systems that handle classified information up to the “Top Secret” level.
- The security controls at this level are the most robust, reflecting the heightened sensitivity and security requirements associated with top-secret information.
Identify Security Controls & Implement Security Controls
The number of controls can vary based on the specific control families and the impact level. Here is a general overview:
|
Impact Level |
Categorization |
Controls |
|
IL2 |
Low | 125 |
|
IL4 |
Moderate |
325 |
|
IL5 |
High | 421 |
| IL6 |
High |
421 with increased sensitivity |
You can download the FedRAMP Security Controls Baseline here.
Create SSP
SSP provides a comprehensive overview of the security controls and measures implemented by a CSP. Below are key details typically included
- System Overview
- System Architecture
- Security Control Implementation Details
- Control Assessment
- Continuous Monitoring
- Incident Response
- Configuration Management
- Access Control
- Security Training and Awareness
- Security Assessment and Authorization
- Data Encryption using FIPS modules
The following figure will give you a sneak peek at what process we followed and what tasks we performed at each stage 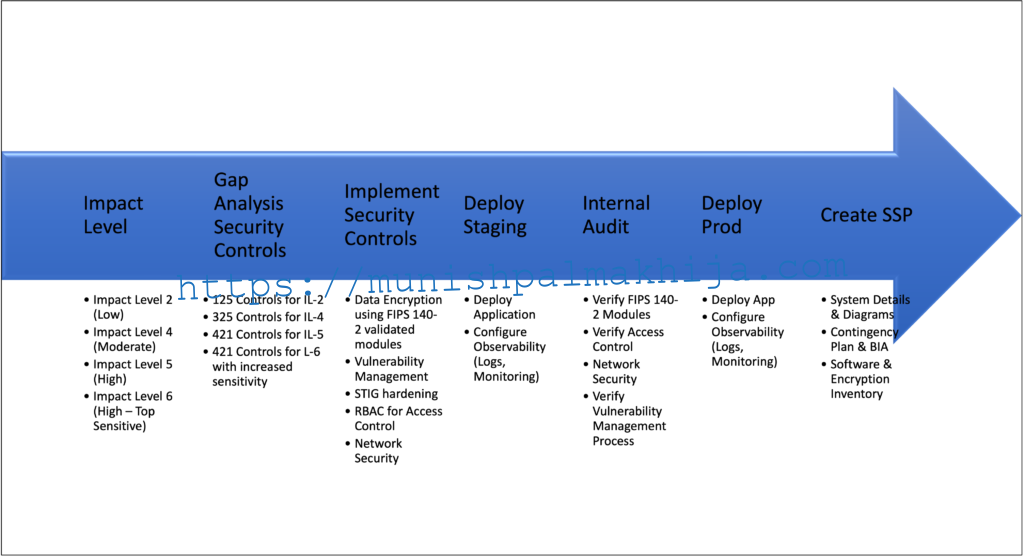
Assess
CSPs must use an independent assessor to test the information system to demonstrate that the controls are effective and implemented as documented in the SSP.
At this point, a third-party assessment organization (3PAO) will develop a security assessment plan (SAP) that outlines the testing approach.
Testing will need to be performed on Production Systems. Once the testing is complete, the 3PAO will issue a Security Assessment Report (SAR) that contains information about vulnerabilities, threats, and risks discovered during the testing process, as well as guidance for your firm in mitigating the security weaknesses discovered.
Authorize
Once testing has been completed, the next step is for AOs to make a FedRAMP Authorization decision based on the completed package of documents and the risks identified during the testing phase.
Continuous Monitoring
Once CSP receives FedRAMP Authorization it must implement a continuous monitoring capability to ensure the cloud system maintains an acceptable risk posture. This process determines whether the set of deployed security controls in an information system remains effective in light of planned and unplanned changes that occur in the system and its environment over time.
Conclusion:
FedRAMP is a valuable program for federal agencies looking to adopt cloud-based services while minimizing risk. By providing a standardized approach to cloud security assessments and authorizations, FedRAMP helps to improve the overall security posture of federal agencies and reduce the risk of data breaches and cyber-attacks. Cloud service providers that comply with FedRAMP can also benefit from streamlined compliance processes, cost savings, and increased confidence in their security controls and procedures. As the use of cloud-based services continues to grow, FedRAMP will play an important role in ensuring the security and privacy of sensitive data.