VMware Aria Operations for Logs Cloud a.k.a. vRLI Cloud is SaaS Service that allows you to manage data at scale and it helps provide deep operational visibility and intelligent analytics for troubleshooting and auditing across private, hybrid, and multi-cloud environments.
As it is a SaaS-based service the billing is based on the logs ingested so it is critical for the admins to know what log sources are ingesting the most to avoid unexpected bills at the end of the month.
In this blog, I will show how easy it is to identify noisy log sources in vRLI Cloud using PowervRLICloud.
What is PowervRLICloud
It is a PowerShell module that abstracts the VMware vRealize LogInsight Cloud APIs to a set of easily used PowerShell functions. This tool provides a comprehensive command-line environment for managing your VMware vRealize LogInsight Cloud environment
Getting Started
Pre-requisites
You need to have the following pre-requisites
- vRealize LogInsight Cloud API Token
- PowerShellVersion = ‘6.0’ and Above
Connect to vRLI Cloud
Connect-vRLI-Cloud -APIToken “APIToken”
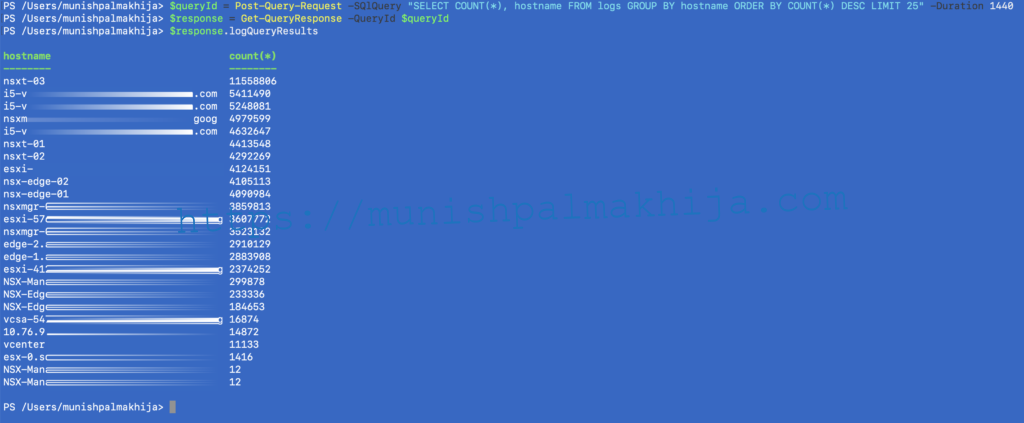
Scenario 1 – Identify log source using hostname field in last 24 hours
$queryId = Post-Query-Request -SQlQuery “SELECT COUNT(*), hostname FROM logs GROUP BY hostname ORDER BY COUNT(*) DESC LIMIT 25” -Duration 1440
$response = Get-QueryResponse -QueryId $queryId
$response.logQueryResults
Note – 1440 mins is 24 hours
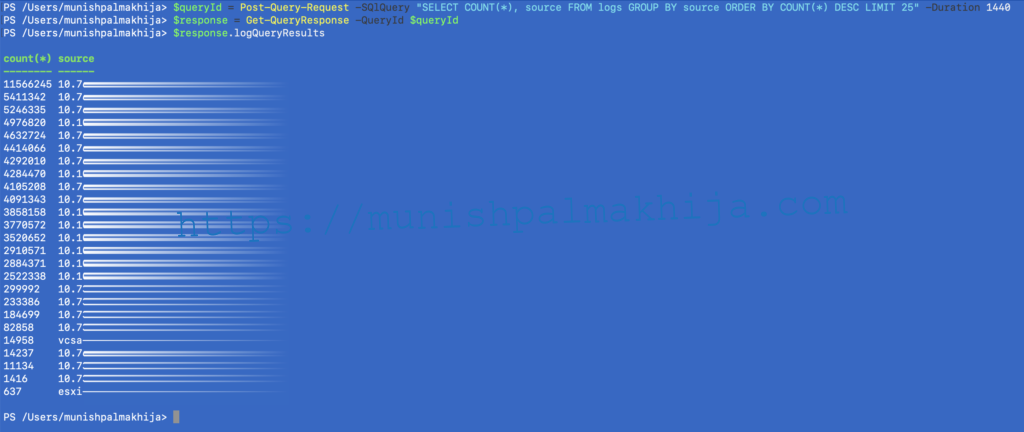
Scenario 2 – Identify log source using source field in last 24 hours
$queryId = Post-Query-Request -SQlQuery “SELECT COUNT(*), source FROM logs GROUP BY source ORDER BY COUNT(*) DESC LIMIT 25” -Duration 1440
$response = Get-QueryResponse -QueryId $queryId
$response.logQueryResults
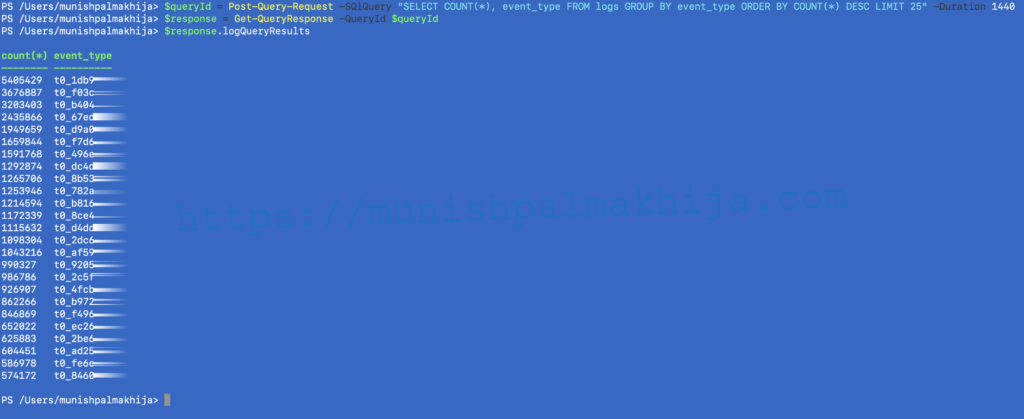
Scenario 3 – Identify log source using event_type field in last 24 hours
Once you identify what log source is sending the most number of logs, the next step would what type of event type it is. vRealize Log Insight Cloud tries to automatically detect groups of similar events based on the number of common parts that the events have. The system uses machine learning to group similar events together, with each group showing the approximate number of events in the group. Grouping events helps identify the most communicative events and the quiet ones, both of which are critical for troubleshooting. For more details, you can refer the documentation
$queryId = Post-Query-Request -SQlQuery “SELECT COUNT(*), event_type FROM logs GROUP BY event_type ORDER BY COUNT(*) DESC LIMIT 25” -Duration 1440
$response = Get-QueryResponse -QueryId $queryId
$response.logQueryResults
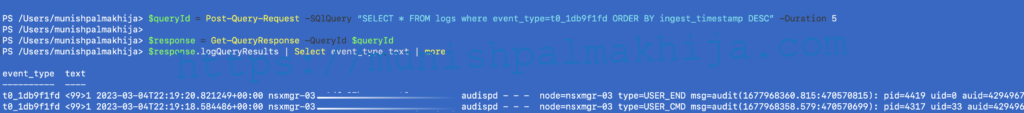
If you want to find more details of even type you can search logs for the specific event type
$queryId = Post-Query-Request -SQlQuery “SELECT * FROM logs where event_type=t0_1db9f1fd ORDER BY ingest_timestamp DESC” -Duration 5
$response = Get-QueryResponse -QueryId $queryId
$response.logQueryResults | Select event_type,text | more
This is how easy it is to identify the noisy log sources and try to avoid surprises in the bill
Try out vRealize Log Insight Cloud
If you’re not already using vRealize Log Insight Cloud, check out our free 30-daytrial. To learn more about how to use Log Insight Cloud, please check out
- VMware Pathfinder.
- VMware Cloud Management Blogs
- VMware Cloud Management You Tube Channel
Related Articles